

This writing presents a framework that if adopted by insurance agencies and carriers could simplify and minimize the cost of complying with the New York Department of Finance Regulation 23 NYCRR Section 500.11 “Third-Party Service Provider Security” while simultaneously deploying and maintaining a controlled environment that adequately protects customer non-public information (NPI).
The New York DFS Cybersecurity Regulation defines “Third-Party Service Provider” as, “a person that is not an affiliate of the covered entity, provides services to the covered entity, and maintains, processes or otherwise is permitted access to nonpublic information through its provision of services to the covered entity.”
From the covered entity’s standpoint, a third-party service provider is somebody who stores, maintains or processes its customer NPI. Section 500.11 requires that covered entities develop processes to ensure that third-parties are adequately safeguarding their NPI, which includes both contractual and procedural due-diligence. The problem is both agents and carriers are covered entities who, by definition, store each-other’s NPI, which means that they are third-party service providers to each other.
This creates a tangled web of random cross due-diligence acts of geometric proportions: carriers on agencies and agencies on carriers; cybersecurity questionnaires of all shapes and sizes bouncing between covered entities like ping-pong balls in a racquetball court. This “many-to-many” condition, combined with the complete and utter absence of New York DFS guidance in this matter caused ever-increasing levels of confusion leading up to the March 15 due-diligence deadlines.
Under the current dysfunctional landscape, agencies – regardless of their size – are finding themselves having to hire new or redirect existing resources to perform tasks that require an administrative skill set that one is not likely to find in a business that sells insurance product. Ultimately, the inclusion of yet another deviation from the producer’s core competency serves only to further erode already razor-thin profit margins.
Next, yet another David and Goliath-type conflict rears its head from the foul depths of the halls of the store-front insurance agency. This conflict isn’t with the New York DFS, instead, it was birthed out of its lair and then reared its head as the carrier.
Under the most conservative interpretation of Section 500.11, it’s difficult to conclude anything other than the notion that producers and carriers are third-party service providers to each other. While still struggling to determine how to secure their respective environments, the New York DFS, in response to an impassioned request from the independent agency community to exclude carriers from agencies’ lists of third-party service providers, published an FAQ stating, “It is also noted that, like any other covered entity, an insurance company may also be a third-party service provider and authorized user with respect to another covered entity, including an independent insurance agent.”
Add another difficult question into an already crowded field of challenges: How do thousands of producers assess and then conclude on the adequacy of the cybersecurity controls of each of their carrier appointments?
Add to this the fact that carriers are not likely to disclose any information about their cybersecurity architecture as doing so is akin to posting their claims reserve bank account statements on Facebook.
Finally, there’s the matter of the form and content of the cybersecurity risk assessment, which most agents and carriers chose to use as their due-diligence process. What does “risk” mean within the context of carrier/producer transactions? Once defined, how do we create an inventory of risks inherent of the carrier/agency business relationship? What questions must I ask, and how do I quantify the responses so that they roll up in the aggregate in a way that enables me to compare respondent risk levels to each other and to track respondent progress in achieving various benchmark risk levels?
Herein lies the elixir that transforms thousands upon thousands of risk assessment responses from an endless, albeit random, procession of ones an zeros into a powerful tool capable of pinpointing both the location of control weaknesses within the entity’s IT architecture and whether the cost of remedying exceeds the cost of accepting.
Imposing comprehensive end-to-end cybersecurity risk management processes upon the average property and casualty insurance agency is like pushing an Uber driver into the cockpit of a 777. It is, plain and simple, not scalable in large part because the regulator’s expectation of compliance far exceeds the target’s aptitude and ability to comply. A framework capable of bridging this gap is one in which a trusted, independent and highly competent third-party intervenes to assess and determine the adequacy of cybersecurity controls used by the service provider to protect NPI are aligned with one or more widely adopted cybersecurity standards.
The regulation defines a third-party service provider in Section 500.01 (n) as “a person that:
The following is a listing of insurance agencies’ most widely used service providers, each of which satisfies all three criteria of third-party service providers itemized in 500.01 (n.)
Insurance agencies use miscellaneous Cloud Providers like Microsoft, Google and Mail Chimp applications. These Cloud-based entities provide word processing, spreadsheet, email and SMS messaging capabilities which are all potential repositories for NPI. While most of these third-party service providers are SOC 2 (service organization controls) certified, they cannot prevent their producer customers from storing customer NPI in clear-text MS Word, Excel, mail and instant messaging files.
Insurance aggregators are third-party vendors who themselves are non-exempt covered entities. Aggregators can demonstrate compliance with NYDFS Section 500.11 by providing summary results of a qualified independent third-party assessment. An attestation of compliance with the NIST 7621 or ISO 27001 cybersecurity frameworks easily meets or exceeds 500.11 due diligence requirements and can therefore act as a proxy for an audit of the service provider by the covered entity.
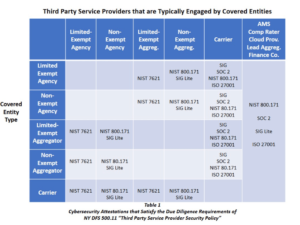
Large third-party service providers like national insurance carriers, engage independent qualified third-party assessors to perform SOC 2 assessments of the effectiveness of controls over of their information systems. While SOC 2 reports are usually available only to management, the public version, called SOC 3, is open to anyone. Producers can quickly acquire and review SOC 3 reports to ensure that the service provider complies with 500.11.
Smaller third-party service providers engage qualified third-party assessors to perform reviews of cybersecurity controls and practices for compliance with the National Institute of Standards and Technology Cybersecurity Control Guidance for small businesses (NIST 7621) and the more comprehensive NIST 800-171 Standard that focuses on the protection of unclassified information in non-federal information systems and organizations.
Cybersecurity controls assessments on covered entities can also be based upon other widely recognized cybersecurity frameworks like SIG, SIG Lite and the ISO 27001. Covered entities should take comfort that their customer NPI is adequately secured by third-party service providers who can demonstrate alignment of their cybersecurity policies, procedures and practices with one or more of these frameworks.
Related: